Author: Brandon Lewis
If you remember the 90s you probably remember the spread of unwanted software and the subsequent proliferation of antivirus/security products from Norton, McAfee, and others. Today’s IoT is similar to those early days of the PC in that security is still playing catch up, but what’s different, according to Stefan Thom of the Trusted Computing Group, is that the ability to remotely update firmware on almost any connected device means we are now surrounded by things we cannot trust.
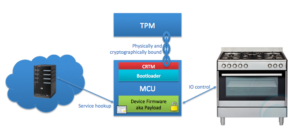
To Thom, connected devices are little more than boxes of metal and plastic that are subject to the whims of the next person who comes along with an Internet connection, leaving the physical hardware itself as all we can rely on. In response, Thom and his colleagues at the Trusted Computing Group have been allocating a significant portion of their resources towards a trusted platform module (TPM) specification that enforces physical or time-based isolation of execution environments; strong device identity through cryptographic endorsement keys; sealed storage; attestation; and policy-bound operation. On modern MCUs these characteristics are implemented through a range of TPM features that include:
- An immutable boot loader (CRTM)
- Secure seeding of an internal PRNG
- Manufacturer-authenticated platform boot
- Measured boot as a tamper-proof record of code and data
- Establishing ownership and device identity generation
- An attestation client that reports the device state
- Confidential storage of device configuration
- Secure identity and data protection key import
- Firmware rollback protection
- Secure forward migration of configuration data
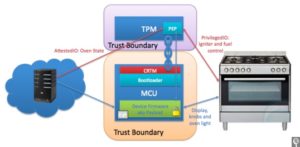
This feature set makes for an architecture such as that shown in Figure 1, but what about securing critical I/O security? This is where the Trusted Computing Group goes a step further by implementing I/O policies that even the MCU cannot override, revoking the MCU’s access to critical I/O if it is in an unknown state. Doing so allows for additional attestation of data that the MCU reads for an added level of trust, and helps to reduce the attack surface of IoT devices overall (Figure 2).


The foundation of IoT security begins at the device level, and measures such as these outlined in the Trusted Computing Group’s Trusted Platform Module 2.0 specification offer a way to build trust in from the start rather than scrambling to add patches after vulnerabilities are discovered. To find out more, visit trustedcomputinggroup.org or look for Stefan’s slides on the IoT Evolution Developers Conference website next week.
To read the full article, please click here.